The notorious Necurs botnet is one of the oldest and largest spam and phishing delivery systems in existence. It controls millions of machines that the criminal botmasters use to send malicious payloads. Necurs has now adopted a retro trick to make itself more evasive and less likely to have its phishing intercepted by your filters.
It's begun emailing archive files that unzip to a file with a .url extension. This commonplace Windows shortcut opens a page directly in a browser. The advantage of this approach is that it's typically overlooked by email scanners, which are hunting for more complicated infection chains. The final destination of this link is a remote script file that downloads and automatically executes a malicious payload.
This common Windows shortcut is the social engineering tactic which tricks your users into thinking the email file attachment they just unzipped has created a folder that they need to enter and view the actual file.
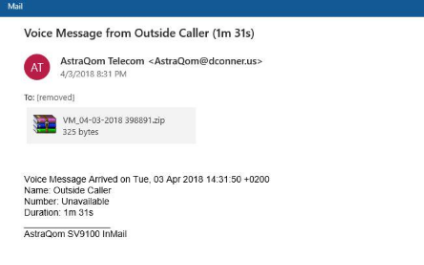
Unfortunately, this is what crooks want because trying to access this faux folder will launch the infection chain. This time, they are exploiting the power of simplicity. Here is how the Phish looks:
Your email filters usually apply preset rules, and this particular vector is probably not among them, so update your filter settings. Interestingly, Necurs does not infect computers using Russian as a language.