CONTACT US:
VA: 703-991-0101,
DC: (202) 517-7710,
MD: (301) 880-4011
SUPPORT CENTER
GRS Technology Solutions
Achieve CMMC Compliance with Confidence
From assessments to implementation, we’ll guide you every step of the way!



Your Trusted Partner for CMMC Readiness

At GRS, CMMC isn't just a service—it’s part of our mission. As a CMMC Registered Provider Organization (RPO), we’re proud to support our nation’s defense by helping businesses like yours meet strict cybersecurity standards with confidence.
Our team includes Certified CMMC Assessors (CCAs) and Certified CMMC Professionals (CCPs) who are trained in the official CMMC methodology. We bring deep expertise and hands-on experience to guide you through every step of the compliance journey.
We don’t just consult—we roll up our sleeves and work alongside you to develop and implement the right security controls, documentation, and processes to get audit-ready.
We live and breathe CMMC—so you don’t have to!
How We Help You Get CMMC Compliant
Our 4-Phase Approach to CMMC Compliance
At GRS, we simplify the path to CMMC by guiding your organization through a structured, proven 4-phase process. From identifying your scope to ensuring long-term compliance, we’re with you every step of the way.
As a Certified CMMC Registered Provider Organization (RPO) with a fully certified team of CMMC Certified Assessors (CCAs) and CMMC Certified Professionals (CCPs), GRS is uniquely equipped to guide you through every step of your CMMC journey. Our structured, hands-on 4-phase approach ensures you’re not just compliant—but fully prepared for assessment and long-term success.
Key Outcomes:
- System Boundary Identification
- CUI Flow Mapping
- Asset Classification
- Scoping Report
Once your scope is clear, we help you build or align your current core documentation required for CMMC compliance. This includes policies, procedures, maintenance checklists, and your System Security Plan (SSP)—all tailored to your business operations and mapped to CMMC practices.
Key Outcomes:
- CMMC-Aligned Policies & Procedures
- System Security Plan (SSP)
- Plans of Action & Milestones (POA&M)
- Evidence Templates
With a clear blueprint in hand, we help you close any identified gaps. Whether it’s configuring systems, enforcing technical controls, or training your team—we work side-by-side with you to bring your environment into full compliance.
Key Outcomes:
- Technical & Administrative Control Implementation
- Security Tool Deployment (e.g., logging, MFA, FDE)
- Process Enablement
- Control Validation
CMMC isn’t a one-time project—it’s a continuous commitment. We offer ongoing support to maintain compliance, monitor for changes, and prepare for your formal assessment. Think of us as your long-term partner in cybersecurity maturity.
Key Outcomes:
- Continuous Monitoring & Logging
- Evidence Collection & Maintenance
- Quarterly Reviews & Control Health Checks
- Pre-Assessment Readiness Support
With years of experience helping DoD contractors, we’ve fine-tuned a structured, efficient process to get you certified faster while minimizing disruptions to your business.
Why Choose GRS Technology Solutions?
CMMC RPO with a dedicated team of CCAs and CCPs
Ready to guide you through every step of your compliance journey.
Tailored Compliance Strategies
Our solutions fit your unique business needs.
Proven Track Record
We’ve helped numerous organizations achieve compliance quickly and cost-effectively.
End-to-End Support
From assessment to implementation, we handle it all.
Preparing for a CMMC Assessment the Right Way
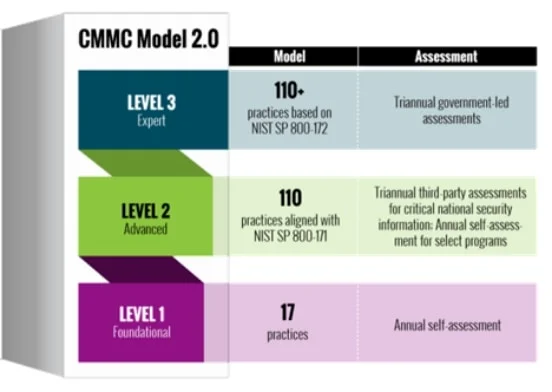
GRS Technology Solutions has provided expert help to DoD contractors in understanding the new CMMC standards and implementing NIST SP 800-171.
Our professionals specialize in helping contractors to prepare for the latest cybersecurity standards in the US.
To avoid any disruption in 2020, contact us today for a free consultation!
Get a CMMC Consultation
